Physical Security: Infiltration
- Chegan SRM

- Jan 28, 2023
- 3 min read
Updated: Oct 19, 2023

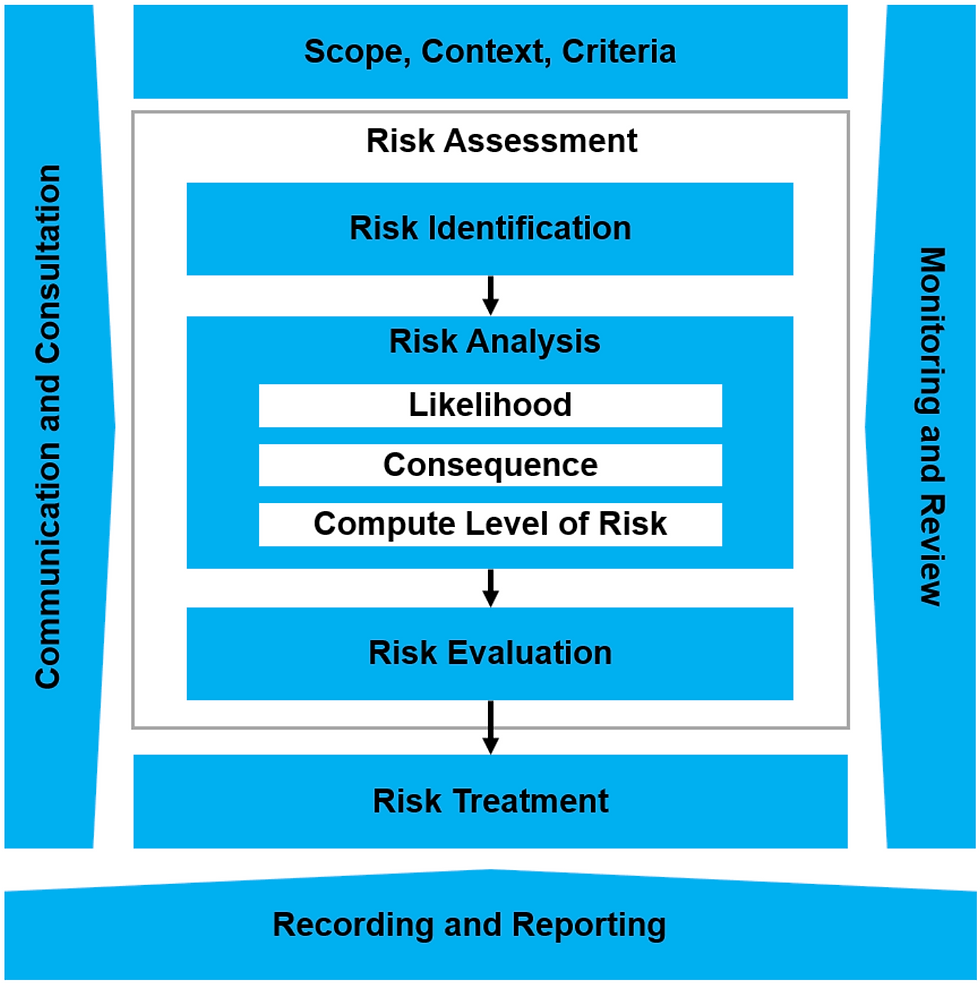
Physical security infiltration is the unauthorized entry of a person or persons into a secure area. Infiltration can be used for the purposes of espionage, sabotage, or other malicious activities, or can involve introducing malicious persons or objects into a secure area. Infiltration can also refer to “penetration testing” or “ethical hacking” in which a security specialist or team of specialists are hired to test a security. The purpose of this test is to identify potential vulnerabilities that could be exploited by a malicious attacker. This test is typically conducted by attempting to gain unauthorized access to an area, analyzing the system for weak spots, and then attempting to exploit any weaknesses found. The results of the test are then used to improve the security of the system and help protect it from potential attacks.
One of the most famous examples of infiltration is the Watergate scandal. In 1972, five men broke into the Democratic National Committee headquarters at the Watergate Complex in Washington D.C. They were attempting to photograph documents and gain access to phone lines in order to listen in on conversations. The burglars were discovered and arrested, and their actions ultimately led to the resignation of President Richard Nixon.
Another example of physical security infiltration is the 2009 theft of the Mona Lisa from the Louvre museum in Paris. On August 21, 2009, Vincenzo Peruggia, an Italian handyman with access to the museum, managed to walk out of the Louvre with Leonardo da Vinci’s masterpiece. He was eventually caught and the painting was recovered after two years. Peruggia’s successful infiltration of the Louvre highlighted the importance of physical security.
An example in the animal kingdom: The cuckoo bird reproduces by sneaking one of its eggs into the nest of a small bird. When the cuckoo chick hatches, it pushes out the other eggs and chicks, so the mother bird will only care for the cuckoo. It also creates a sound that tricks the mother bird into searching for food constantly. Eventually, the cuckoo chick grows bigger than the mother bird and the nest. Once it reaches this size, it then abandons the nest, leaving the mother bird with an empty nest.
Infiltration can have a major impact on an organization. It can lead to the theft of valuable assets, destruction of property, and disruption of operations. It can also lead to financial losses as a result of stolen or damaged goods. Additionally, it can lead to reputational damage if the organization is unable to protect its assets. Finally, physical security infiltration can lead to legal action if the breach results in the loss of customer data or other data breaches.
Countermeasures include the use of locks, alarms, CCTV cameras, security guards and:
1. Access control: Establishing policies and procedures for who is allowed access to physical premises and areas.
2. Surveillance: Utilizing security cameras and other monitoring devices to detect suspicious activity.
3. Intrusion detection: Installing motion sensors, alarms, and other devices to detect intrusions.
4. Secure locks: Using strong locks and keycodes to limit access to certain areas.
5. Visitor management: Implementing a system to track visitors and keep track of who is on the premises.
6. Background checks: Performing background checks on personnel who will have access to sensitive areas.
7. Physical barriers: Installing fences, gates, and other physical barriers to limit access to certain areas.
8. Awareness training: Providing employees with training on how to recognize and respond to potential security threats.
Additionally, organizations should regularly review security protocols and update them as needed.
See also:
Are you looking for a way to protect your business from potential infiltration?
Our services can help you ensure that your business is safe from unwelcome intrusions.
Our team of experienced security professionals can provide you with tailored solutions to mitigate the risk of infiltration. We will assess your business’s security needs and suggest the most effective measures, such as installing locks, alarms, CCTV cameras, and security guards, to protect your premises.
We will also help you stay up to date on the latest security technology and assess any potential weaknesses in your current system.Our services are designed to provide you with peace of mind, knowing that your business is safe from unwanted intrusions. We understand that the safety of your business is a top priority and we are dedicated to providing you with the best protection possible. For more information, please contact us.